Why Traditional Security No Longer Works
The Case for Zero Trust
ZERO TRUST
2/7/20251 min read
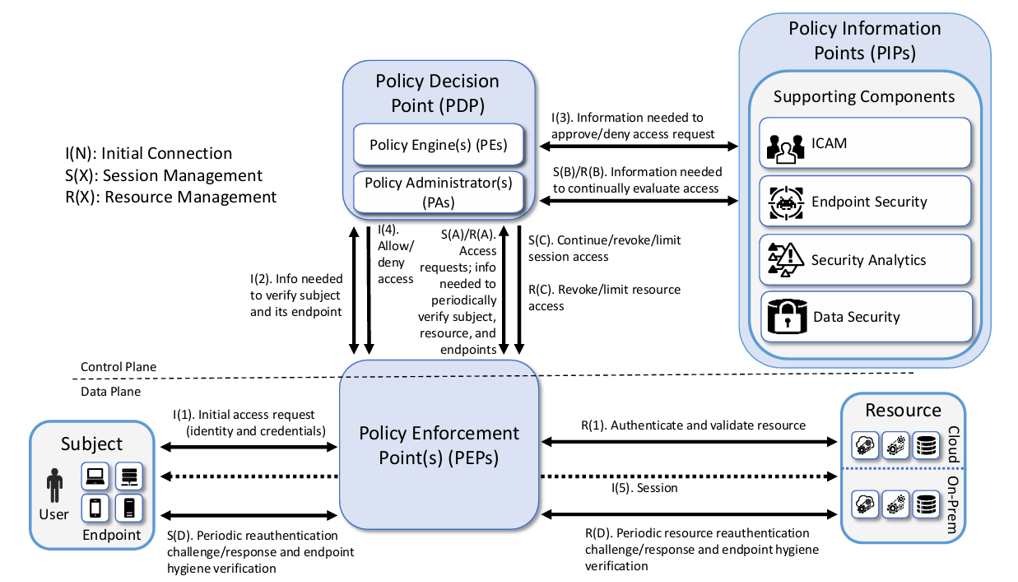
Why Traditional Security No Longer Works – The Case for Zero Trust
For decades, businesses have relied on perimeter-based security: build a strong firewall, secure the network, and assume everything inside is safe. But in today's cloud-first, remote-friendly world, this model is outdated and dangerous. The reality? The perimeter is gone.
The Problem with Traditional Security
1️. Remote Work & Cloud Services – Employees access data from anywhere, often outside traditional network defenses.
2️. Insider & Third-Party Risks – 70% of breaches now involve credentials, meaning attackers can bypass traditional defenses.
3️. Ransomware & Advanced Threats – Cybercriminals exploit weak access controls, moving laterally through systems once inside.
🔴 Recent attacks prove one thing: Trust is a vulnerability. If an attacker gains access, traditional security models assume they belong, leading to massive data breaches.
The Zero Trust Approach: Assume Breach, Verify Everything
Zero Trust eliminates implicit trust and shifts security to a "never trust, always verify" model. It applies three key principles:
✅ Verify Explicitly – Always authenticate and authorize every access request.
✅ Use Least Privilege Access – Users, apps, and devices get only the minimum access needed.
✅ Assume Breach – Continuously monitor and respond to threats as if attackers are already inside.
Why Business Leaders Should Care
🔹 Reduces risk of costly breaches – Prevents unauthorized access before damage occurs.
🔹 Strengthens compliance – Aligns with frameworks like NIST, CISA, and GDPR.
🔹 Enhances workforce security – Secures remote workers without slowing productivity.
What’s Next?
Traditional security can’t protect today’s business landscape—it’s time for a mindset shift. In our next post, we’ll break down what Zero Trust really is (hint: it’s not just a product) and how to begin implementing it without disrupting your business.
Is your organization still relying on outdated security models?


